Tim Lloyd’s Hack Attack and Omega Engineering Forensic Files case serves as a cautionary reminder about how the heat of the moment and the ripple effect of vengeance makes a dangerous combination.
It’s a lesson in the value of integrity and trust, as well as the human cost of betrayal. And how our actions, no matter how insignificant they appear to be or silly, all have consequences.
And those consequences can sometimes alter the course of many lives.
Summary of Tim Lloyd and Omega Engineering Case of Hack Attack Forensic Files
| Field | Case Information |
|---|---|
| Date of Incident | July 31, 1996 |
| Region and Location | Bridgeport, New Jersey |
| Forensic Files Case | Hack Attack (Season 8, Episode 39) |
| Victim | Omega Engineering Inc. |
| Suspects | Tim Lloyd |
| Culprit | Tim Lloyd |
| Type of Crime | Computer Sabotage, Corporate Espionage |
| Forensic Evidence | Malicious “time bomb” code, backup tapes, computer equipment from Lloyd’s home |
| Forensic Techniques Used | Digital data recovery, computer forensic examination, analysis of malicious code |
| Charged For | Computer Sabotage |
| Punishment | 41 months in prison, $2 million in restitution |
| Where is Now | No specific data |
On July 31st, 1996, Omega Engineering, a company known for manufacturing high-tech computer devices for esteemed clients like NASA and the U.S. Navy faced a crisis.
As employees began their day, they were met with a computer message flashing “fixing.” But within moments, the entire computer system crashed. This leads to the deletion of over 1,000 system programs that were the backbone for creating 25,000 different products.
The heart of the company had stopped beating.
To deal with this type of situation, Omega engineers usually take backups. And this was what they did. The plant manager tried to retrieve the backup tape from the filing cabinet.
But the backup tape was missing.
Without it, the original program couldn’t be stored. In this case, the plant was only operational until it ran out of raw materials.
In the midst of this chaos, the name Tim Lloyd surfaced. He was the former network administrator. He was the one who built, maintained, and secured the entire computer network. However, he left Omega three weeks before the incident and no longer had direct access to the system.

Meanwhile, Omega hired Kroll Ontrack, a company that specialization in restoring deleted data from hard drives.
Bob Hackett, a computer forensic expert, began his investigation. The physical drive was intact, but the data was fragmented and mostly unintelligible.
As the investigation deepened, the Secret Service got involved. For digital analysis, they first make a replica of Omega’s hard drive to prevent any manipulation of data.
The findings were shocking.
It wasn’t just deleted; it was purged. This makes recovery nearly impossible.
But, it was not accidental. It was well-planned and strategically purged. This only means that it was an insider job.
Attention returned to Tim Lloyd. He was the one who knows the system well as he was the one that designed it at first.
But he leaves the Omega. So, the secret service tends to seek answers to why he leaves the company.
What they got looked like a case of vengeance. They found Lloyd had faced disciplinary actions for conflicts with coworkers.
Soon, they get a warrant against Lloyd. They searched his house and found piles of computer equipment and suspiciously labeled backup tape. However, the tape was completely blank.
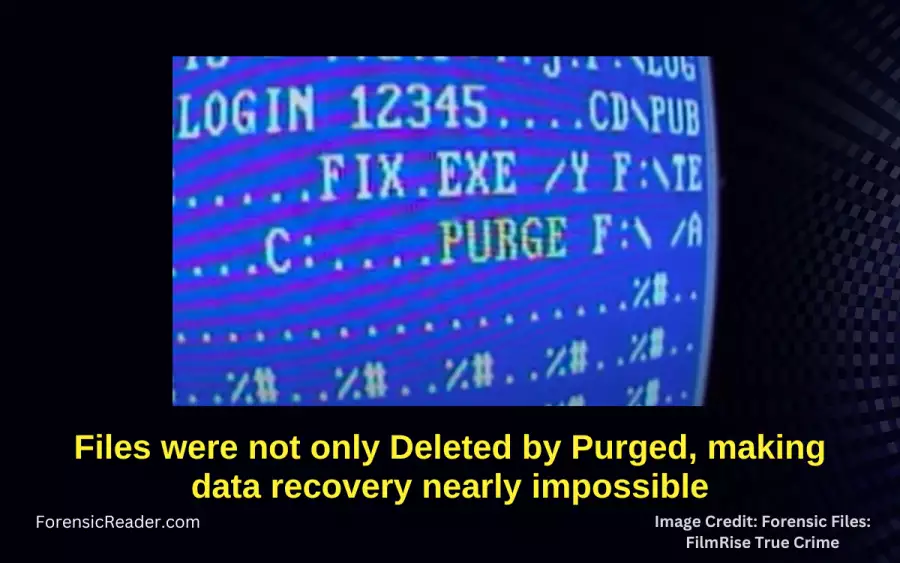
Finally, forensic computer experts found what causes the Omega crisis. It was a malware execution program commonly called “time bomb” software. As the name suggests, they activate when a given condition is met, and in the case of Omega, it was a specific date (July 31st, 1996) that activated the code to delete and purge essential data.
Evidence links Lloyd to crime. Investigators found the same code on one of Lloyd’s hard drives at home. There was also a note stating “Everybody’s job at Omega is in Jeopardy.” even before Omega knows.

Finally, Lloyd was arrested and charged with sabotaging computer systems owned by Omega. And after a four-week trial, found guilty and sentenced to 41 months of prison time. He also had to pay $2 million in restitution.
However, for Omega it cost $10 million of loss with an additional $2 million in reprogramming costs. The company also had to lay off 80 employees.
Who Was Tim Lloyd, His Life, and Conviction?
Tim Lloyd (39) was a systems administrator by profession. He was the mastermind behind a devastating computer sabotage at Omega Engineering which cost them a significant financial and operational loss.
Here is more information about him:
- Professional Background & Expertise: Tim Lloyd was not just an employee; he was the architect of Omega Engineering’s computer network and programming.
- How long Lloyd worked for Omega: He dedicated over a decade, precisely 11 years. He was once considered the backbone of the company.
- Trust & Reliability: Within the company, Lloyd was one of the trusted members. As per the report, Omega sees him as “a trusted member of the family.” His dedication and work for more than a decade had earned him this reputation.
- Conflict at Workplace: Lloyd had faced disciplinary actions due to conflicts with coworkers. These incidents hinted at underlying tensions.
Tim Lloyd’s Conviction:
- Location of Conviction: Convicted in U.S. District Court in Newark, N.J.
- Reason for Conviction: Lloyd was found guilty of planting a “software time bomb” in Omega’s computer system which resulted in the deletion and purging of essential data.
Charges and Punishment Against Tim Lloyd:
- Main Charge: Sabotaging computers under federal law for computer-related crime.
- Prison Sentence: A sentence of 41 months in federal prison.
- Restitution: $2 million in restitution to Omega Engineering as compensation for the damages Lloyd caused.
Reasons Why Tim Lloyd Sabotaged Omega Engineering’s Computer System?
These are the three main reasons why Tim Lloyd was involved in the case:
Reason 1: Power and Control Over the System
- Tim Lloyd was the architect of Omega Engineering’s computer network.
- His role was pivotal, overseeing the system that was the backbone of the company’s operations.
Reason 2: Past Conflicts and Disciplinary Actions
- Lloyd had faced disciplinary actions due to conflicts with coworkers.
- These disciplinary actions harbored personal grudges against certain individuals or the company.
- Potential Resentment: The disciplinary actions and conflicts might have sown seeds of resentment.
- Acting out against the company as a form of revenge.
Reason 3: A Desire to Prove Technical Prowess
- A deeper desire to prove his technical prowess. Lloyd might have wanted to demonstrate his capabilities in a destructive manner.
- Psychological Profile: The meticulous planning and execution of the sabotage hint at a deeper motive.
- Perhaps a desire to leave the company in disarray as a testament to his importance.
- Masking the Sabotage: The code was masked to show “fixing” while causing destruction. Indicates a desire to not just harm but also deceive.
[Table] Forensic Evidence Against Tim Lloyd in Hack Attack Case
| Evidence Type | Location | Significance in the Case |
|---|---|---|
| “Time Bomb” Code | Omega’s Centralized File Server | Responsible for the deletion and purging of essential data, leading to the catastrophic crash of the system. |
| Deleted vs. Purged Data | Omega’s Hard Drive | Revealed that the data was not just deleted but purged, making recovery nearly impossible and indicating sabotage. |
| Backup Tapes | Missing from Omega | Should have contained crucial programs but were mysteriously missing, further complicating recovery efforts. |
| Digital Replica of Hard Drive | Created by Secret Service | Allowed for a thorough examination without tampering with the original data. |
| “Time Bomb” Code (Duplicate) | Tim Lloyd’s Personal Hard Drive | Matched the malicious code found in Omega’s system, directly linking Lloyd to the sabotage. |
| Backup Tape with Pertinent Date | Tim Lloyd’s Residence | Though the tape was blank, the dates were significant and tied back to the timing of the sabotage. |
Forensic Experts and Investigators in the Case
| Expert Names | Roles |
|---|---|
| Sharon Gaudin | Editor, Datamation.com |
| V. Grady O’ Malley | Assistant U.S. Attorney |
| Sac James J. Borasi | U.S. Secret Service |
| Bob Hackett | Computer Forensics Expert |
| Greg Olson | Computer Forensics Expert |
| SA Pat Pruitt | U.S. Secret Service |
Forensic Analysis and Techniques Used in Hack Attack Forensic Files Case

1. Prevent Data Modification
Technique used: Write blockers. There are two types: hardware and software-based.
- Hardware-based write blockers: UltraBlock, Digital Intelligence Ultrakit, Tableau UltraBlock SAS Write Blocker, etc.
- Software-based write blockers: require a bootable DVD or USB drive that runs an independent OS.
When Used: Always where data-related hardware evidence is needed to further analyses by digital forensic means.
How this technique Works: It prevents any modification, even a single bit of data, of original data in hard drives or other storage devices.
Significance in the case: Secret Service used it to prevent any modification of data before it was cloned.
2. Cloning of Hard Drive
Technique used: Bit-by-bit cloning with unique identifier hash (MD5 or SHA-1) to define an exact replica of the original drive. One most used software is AccessData FTK Imager Lite.
When used: Common in computer forensics when data needs to be analyzed from storage devices such as hard drives, SSDs, micro-SD cards, floppy disks, etc.
How this technique works: An exact digital replica of the original hard drive which was later used for examination purposes.
Significance in the case: The Secret Service made a clone of Omega’s hard drive to ensure that the original data wasn’t altered during the investigation.
3. Data Recovery and Analysis
Technique Used: Redundant array of independent disks (RAID) for hard drives or other specialized software.
When used: Recovery of deleted or last data especially from hard drives.
How this technique works: Forensic experts search for traces of deleted or altered data on each sector of the hard drive.
RAID is either built-in or in the system itself. Its main work is to minimize data loss caused by disk failure. More information related to RAID:
- RAID: Stands for Redundant Array of Independent Disks.
- Configuration: Involves two or more physical disks.
- Original Purpose: Developed to minimize data loss from disk failure.
- RAID Levels: Can be implemented through software or special hardware controllers.
- Software RAID: Implemented from the host computer’s OS.
- Hardware RAID: Uses its own controller, processor, and memory connected to the host computer.
Significance in the case:
- Investigators discovered programs on Omega’s server were not just deleted but purged with deliberately “PURGE” command.
- They also found evidence of test runs of the malicious code.
Read More: Mobile Forensic Data Acquisition Methods and Tools
4. Virus Detection and Analysis
Technique used: Software-based blockers that resist any further modification or execution of code suspecting the system has been compromised by malicious software.
How this technique is used: Experts scan the system for signatures or behaviors typical of known viruses or malware.
Significance in the case: No viruses were responsible for the damage to Omega’s computer system.
5. Code Analysis
Technique used: Cloned hard drive and a forensic expert for analyzing and reading data bit by bit in digital form.
How this technique works: Forensic experts examine lines of code to determine their function and potential impact on a system.
Significance in the case:
- Investigators found the malicious “time bomb” code responsible for the deletion and purging of Omega’s data.
- It was set to execute on a specific date.
- This code was linked back to Tim Lloyd, providing crucial evidence for the case.
Read More: Mobile Device Forensic: Ultimate Guide for Collection
My Thoughts on Tim Lloyd’s Case of Hack Attack Forensic Files
Tim Lloyd has a great knowledge of his field. He was the one that created a fabulous program that was key to the success of Omega Engineering Inc. in the 1990s.
However, betraying the trust of colleagues, friends, and an entire organization is no small feat. It begs the question: What drives someone to such extremes?
The most obvious one is vengeance and betrayal.
They can cloud judgment and make the consequences of one’s actions appear insignificant in the heat of the moment.
But why would anyone risk it all, especially when the consequences are so severe?
In Lloyd’s case, it wasn’t just his future at stake but the livelihoods of 80 other employees.
Is Tim Lloyd a different person now? It’s a possibility. People can and do change. But, the path of redemption is long and challenging. It is full of genuine remorse and commitment to do better for others.
And only Lloyd knows whether or not he has started on this journey.
What are your thoughts? Do you believe in second chances and redemption? Or do you think some actions are simply unforgivable? Let’s discuss this further in the comments.
Read Similar Case: Jason & Ken MacLennan Case [Shoot to Thrill] Forensic File Case Study
General FAQs About Tim Lloyd’s Case
What was the specific “time bomb” code that Tim Lloyd used?
The “time bomb” code was a malicious piece of software designed to activate on a predetermined date which was July 31st, 1996. When triggered, it purged essential data from Omega’s server, rendering over 1,000 programs inoperative.
How did Omega Engineering first realize it was sabotage and not a typical system failure?
Omega initially thought it was a system failure. However, when recovery attempts failed and backup tapes were missing, suspicions arose. The involvement of forensic experts from Kroll Ontrack revealed the data was purged, not just deleted, hinting at deliberate sabotage.
Were there any signs or warnings before the system crashed?
The computer display only flashes a sign before the crash was a message displaying “fixing.” This was just a deception of the execution of the “time bomb”, which made it appear to be a routine process while deleting critical data.
Did Tim Lloyd have any accomplices or was he acting alone?
Tim Lloyd acted alone based on the evidence and proceedings of the case. There is no evidence that he had any help in the sabotage.
Was there any specific reason Lloyd chose the date he did for the “time bomb” to activate?
I believe this is due to two factors. The first is that he does not want to be suspected after leaving the company. And the date of July 31st, 1996, may have been a memorable one, as the last working day of the month.
References:
- Watch full episode Forensic Files – Season 8, Episode 39 – Hack Attack [YouTube]
- The Omega files: A true story [CNN]
- Man Charged With Sabotage Of Computers [NyTimes]
- Guide to Computer Forensics and Investigations by Bill Nelson, Amelia Phillips, Christopher Steuart · 2014 [Google Books]
- Another case where computer forensic is used: Alan & Miriam Helmick Case [Gone Ballistic]

FR Author Group at ForensicReader is a team of Forensic experts and scholars having B.Sc, M.Sc, or Doctorate( Ph.D.) degrees in Forensic Science. We published on topics on fingerprints, questioned documents, forensic medicine, toxicology, physical evidence, and related case studies. Know More.

